On June 1, the Ontario Energy Board released the proposed Cyber Security Framework for the Ontario electricity sector, along with a set of related documents. The Cyber Security Framework, developed over the previous year in consultation with electricity stakeholders, is expected to establish standards and structure for much of the Ontario electricity industry’s approach to protection against cyber threats. At the same time, the Board released its staff paper on the proposed Cybersecurity Framework (CSF) for the Ontario electricity sector, and a 108-page white paper on the framework.
 Development of the CSF in consultation with industry has been underway for more than a year. On February 11, 2016 the Ontario Energy Board initiated a consultation to review the cybersecurity of the non-bulk electrical grid and associated business systems in Ontario in respect of grid reliability, cyber-attacks, and the protection of personal information. Distributors would be required to ensure their system plans include appropriate consideration of such risks based on industry best practices. As the staff report points out, unlike the bulk electrical system, where NERC Critical Infrastructure Protection (CIP) standards apply, non-bulk transmission and distribution systems do not have a standard or framework focused on cyber security and privacy risks for the sector.
Development of the CSF in consultation with industry has been underway for more than a year. On February 11, 2016 the Ontario Energy Board initiated a consultation to review the cybersecurity of the non-bulk electrical grid and associated business systems in Ontario in respect of grid reliability, cyber-attacks, and the protection of personal information. Distributors would be required to ensure their system plans include appropriate consideration of such risks based on industry best practices. As the staff report points out, unlike the bulk electrical system, where NERC Critical Infrastructure Protection (CIP) standards apply, non-bulk transmission and distribution systems do not have a standard or framework focused on cyber security and privacy risks for the sector.
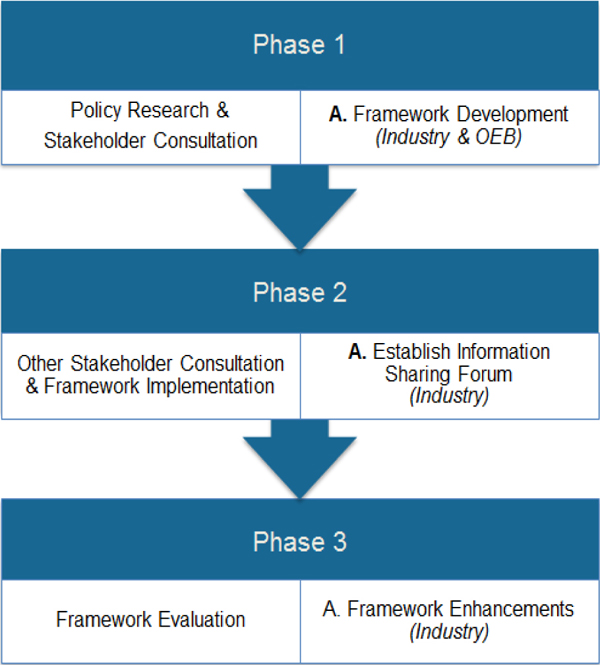 Phase 1 of the consultation focused on distributors’ requirements, with a framework expected to be in place in late 2017. OEB staff has proposed interim reporting by LDCs on cyber security assessment and progress within three months of the framework being issued, and an annual certification of cyber security capability starting in 2018. New industry working groups would be set up to facilitate the continuous improvement of the Framework.
Phase 1 of the consultation focused on distributors’ requirements, with a framework expected to be in place in late 2017. OEB staff has proposed interim reporting by LDCs on cyber security assessment and progress within three months of the framework being issued, and an annual certification of cyber security capability starting in 2018. New industry working groups would be set up to facilitate the continuous improvement of the Framework.
In the next phase, OEB staff is proposing establishment of a Cyber Security Information Sharing Forum (CSIF), and recommending the ongoing evolution of the framework be undertaken by an industry-led Cyber Security Advisory Committee (CSAC).
To assist it in developing a framework, the OEB established two consultative groups: a Steering Committee and a Cyber Security Working Group (CSWG) comprising licensed electricity distributors, representatives of the Ontario Ministry of Energy, IESO, the Electrical Safety Authority and natural gas utilities. The OEB also retained industry leading consultants Acumen Engineered Solutions International (AESI), augmented by DLA Piper (Canada) LLP and Richter LLP, to work with the CSWG.
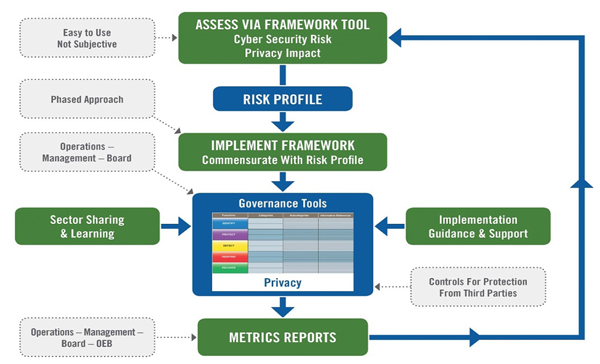
Recommendations for the framework include leveraging a leading framework already in use in critical sectors, and minimizing duplication of effort for distributors that already have advanced measures in place. The NIST framework (among its three components, only its core: Identify, Protect, Detect, Respond, and Recover) has been chosen as the foundation for the proposed framework. NIST, however, does not include privacy in its guidelines, so that Privacy by Design (PbD) principles have also been embedded into the proposed framework.
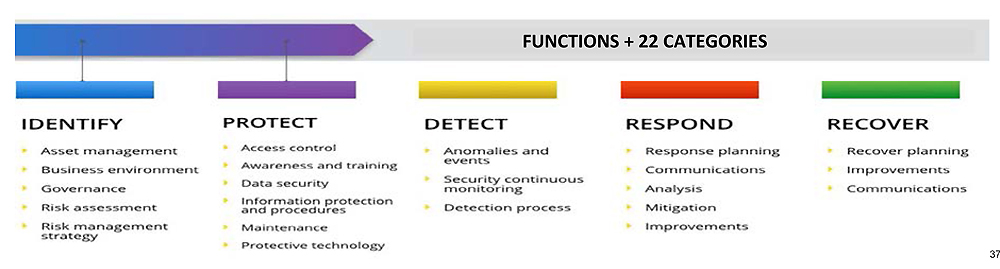 22 cyber security functions in five categories, identified by the National Institute of Standards and Technology Framework (NIST)
The Cyber Security Framework begins with a Risk Profile Tool, developed with input from the Cyber Security Working Group and specifically tailored to the inherent risks in Ontario’s LDC community. The Risk Profile Tool allows each Ontario LDC to be categorized based on their inherent risk, in an objective fashion. Based on size, maturity and capability, Ontario LDCs will have different inherent risk profiles, defined as High, Medium or Low (baseline). Each risk profile will require that a varying degree of security controls be applied to ensure an adequate level of security.
22 cyber security functions in five categories, identified by the National Institute of Standards and Technology Framework (NIST)
The Cyber Security Framework begins with a Risk Profile Tool, developed with input from the Cyber Security Working Group and specifically tailored to the inherent risks in Ontario’s LDC community. The Risk Profile Tool allows each Ontario LDC to be categorized based on their inherent risk, in an objective fashion. Based on size, maturity and capability, Ontario LDCs will have different inherent risk profiles, defined as High, Medium or Low (baseline). Each risk profile will require that a varying degree of security controls be applied to ensure an adequate level of security.
Interested stakeholders were invited to submit comments, with a deadline of July 15.
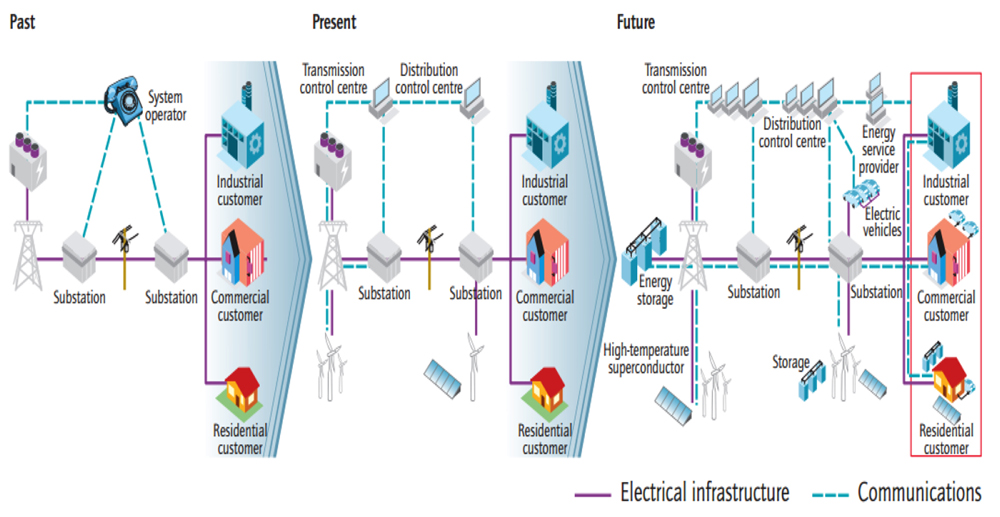 As the grid has gotten smarter, more interconnected, more automated, and learned to incorporate distributed generation and semi-autonomous microgrids, each connection has added a potential access point for security breaches, cyber-attacks and cyber-crime. Many experts expect threats and attacks to increase in “intensity & complexity” over the next several years.
A July 6 article by Bloomberg reported that “[h]ackers working for a foreign government recently breached at least a dozen U.S. power plants, including the Wolf Creek nuclear facility in Kansas, according to current and former U.S. officials, sparking concerns the attackers were searching for vulnerabilities in the electrical grid. ... The chief suspect is Russia, according to three people familiar with the continuing effort to eject the hackers from the computer networks.”
As the grid has gotten smarter, more interconnected, more automated, and learned to incorporate distributed generation and semi-autonomous microgrids, each connection has added a potential access point for security breaches, cyber-attacks and cyber-crime. Many experts expect threats and attacks to increase in “intensity & complexity” over the next several years.
A July 6 article by Bloomberg reported that “[h]ackers working for a foreign government recently breached at least a dozen U.S. power plants, including the Wolf Creek nuclear facility in Kansas, according to current and former U.S. officials, sparking concerns the attackers were searching for vulnerabilities in the electrical grid. ... The chief suspect is Russia, according to three people familiar with the continuing effort to eject the hackers from the computer networks.”
