In an August 2019 report, the U.S. Government Accountability Office warns that the electric grid faces significant cybersecurity risks. Although the analysis referred specifically to the US grid, it obviously has implications for Canada’s deeply interconnected grid as well.
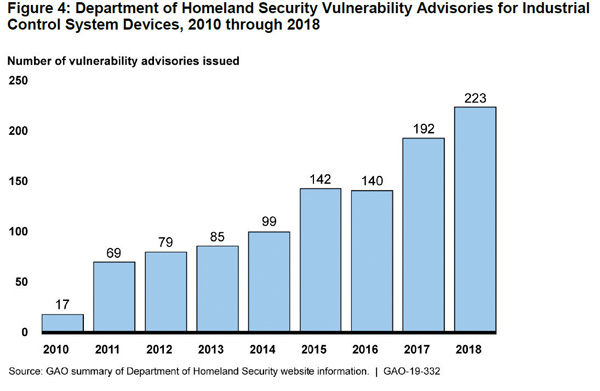 Threat actors are becoming increasingly capable of carrying out attacks on the grid, it says, while at the same time the grid is becoming more vulnerable to attacks. The opportunities to attack industrial control systems are increasing, because tools for exploiting industrial control system vulnerabilities are becoming more available, and at the same time vulnerabilities and potential points open to attack have been multiplying. The report identifies these and other vulnerabilities among industrial control systems, consumer Internet of Things (IoT) devices connected to the grid’s distribution network, and even the global positioning system (GPS).
Threat actors are becoming increasingly capable of carrying out attacks on the grid, it says, while at the same time the grid is becoming more vulnerable to attacks. The opportunities to attack industrial control systems are increasing, because tools for exploiting industrial control system vulnerabilities are becoming more available, and at the same time vulnerabilities and potential points open to attack have been multiplying. The report identifies these and other vulnerabilities among industrial control systems, consumer Internet of Things (IoT) devices connected to the grid’s distribution network, and even the global positioning system (GPS).
The report goes on to point out that “cheaper and more widely available devices that use traditional IT networking protocols are being integrated into industrial control systems. The use of these protocols, as well as traditional IT computers and operating systems, has led to a larger cyberattack surface—the different points in a network where attackers can try to enter or extract information—for the grid’s systems.
“In particular, many industrial control system devices include remote access capabilities, and industrial control systems are increasingly connected to corporate business networks.
“Industrial control systems, which were once largely isolated from the internet and business IT systems, are increasingly connected in modern energy systems, allowing cyberattacks to originate in business IT systems and migrate to industrial control systems.
“Compounding the risk associated with the increased attack surface, many legacy industrial control systems were not designed with cybersecurity protections because they were not intended to be connected to networks, such as the internet. For example, many legacy devices are not able to authenticate commands to ensure that they have been sent from a valid user and may not be capable of running modern encryption protocols. In addition, some legacy devices do not have the capability to log commands sent to the devices, making it more difficult to detect malicious activity.
“Further, even if owners and operators are able to identify industrial control system cybersecurity vulnerabilities, they may not be able to address those vulnerabilities in a timely manner because certain industrial control system devices may have high availability requirements to support grid operations. These devices typically need to be taken offline to apply patches to fix cybersecurity vulnerabilities. In addition, grid owners and operators need to rigorously test the patches before applying them.
“Moreover, supply chains for industrial control systems can introduce vulnerabilities that could be exploited for a cyberattack. For example, there is a potential for manufacturers and developers to — wittingly or unwittingly — include unauthorized code or malware in industrial control system devices and systems that provides a back door into the equipment or that allows the program to “call home” once installed.”
To this point, the report notes, while there have been cybersecurity “incidents,” none have to this point caused a domestic power outage. Ontario’s Independent Electricity System Operator announced a cybersecurity forum to stay abreast of the issue in July of 2018, and has initiated a sector-wide data-sharing service to help increase the sector’s cybersecurity resilience.
